PDPA: PROTECTING AGAINST THE CYBER PANDEMIC
The pandemic has forced many organisations to digitalise and set up work from home arrangements for their employees. However, most of them are unaware and unprepared for the accompanying risks and vulnerabilities, causing many to fall victim to cyberattacks. This article aims to set out the most common cyber threats that organisations face, as well as basic measures that can be taken so as to comply with the Personal Data Protection Act (PDPA).
Most of the cyberattacks stem from the breach of section 24 of the PDPA (the Protection Obligation), which requires companies to put in place reasonable security arrangements to protect the personal data:
“An organisation must protect personal data in its possession or under its control by making reasonable security arrangements to prevent:
(a) unauthorised access, collection, use, disclosure, copying, modification or disposal or similar risks; and
(b) the loss of any storage medium or device on which personal data is stored.”
It is important to note that under the law, organisations now required to report breaches that pose a significant risk of harm (e.g. financial or physical harm), or if it affects the data of 500 people or more.
As of 20 April 2020, 72% of all published cases, or 100 cases, involved the Protection Obligation.
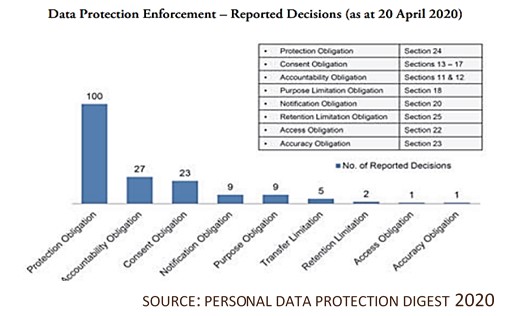
Such problems generally stem from the lack of proper policies and procedures in the company to protect personal data, which contributes to a lack of employee awareness on cyber security protocols and increased susceptibility to external threats. The three main causes for data breach incidents can be attributed to the following causes:
- Human error
- Technical errors
- Malicious activity
1. HUMAN ERROR
Data breach incidents involving human error can often be attributed to the lack a workplace culture of data protection security. Some examples include sending out emails or letters containing sensitive personal data to unintended recipients, as well as misplacing or improperly disposing of data storage devices containing personal data. Such organisations generally do not have adequate data protection policies and procedures such as employee training, or a data protection policy with practical guidance for employees when handling personal data.
It is important to note that under section 53(1) of the PDPA, organisations are held liable for data incidents even if the unauthorised disclosure was caused by an inadvertent mistake made by its employee. Therefore, it is incumbent on the company to implement the proper policies and hold employees accountable for their conduct.
To minimise the occurrence of human errors, the PDPC has, in various enforcement decisions, encouraged organisations to do the following:
- Have a well-documented written data protection policy, and conduct data protection training for employees with regular refresher courses. Practical guidance can also be given to employees who are tasked with handling personal data.
- Automating tasks that involve routine handling and processing of personal data to minimise error. However, such processes should be checked regularly to ensure their accuracy and reliability.
- Implement additional monitoring and verification measures to minimise the risk of accidental mistakes e.g. having second-layer or randomised checks on processes that deal with personal data.
Regardless of their size, organisations should implement internal policies and practices, which should be communicated to employees. In designing the data protection policy, the size of the organisation is but one determinant of the complexity of the internal policies and practices required. The type and amount of personal data the organisation possesses and controls are other relevant considerations.
2. TECHNICAL ERRORS
With the move towards digitalisation, organisations scramble to move their operations online without the requisite knowledge or awareness about the cybersecurity risks that they would be exposed to. Therefore, they are often unaware of the inherent vulnerabilities in the system until the data breach incident has occurred, by which time the damage caused would have been irreparable.
Based on the reported cases, it appears that most of the technical errors stem from the errors or bugs in the programming code of the websites, databases or other software that is deployed to handle the organisation’s personal data. This has often resulted in the personal data being inadvertently made accessible to the public.
In this regard, the PDPC has clarified as to what it considers to be reasonable security arrangements:
- Organisations should conduct vulnerability scans and penetration tests in addition to the standard functional tests to detect vulnerabilities before rolling out any new IT system or process.
- Organisations should consider implementing a second layer of authorisation or verification to obtain access to the personal data where the system or software allows authorised individuals to access personal data through an identifier.
- Organisations should implement access controls should be put in place to prevent personal data from being accessed by unauthorised users or indexed by web crawlers either by placing personal data in a non-public folder/director or putting in place access restrictions.
- Instead of relying on default settings, organisations can “harden” the system configuration by changing the firewall configuration and web server configuration.
It is important to note that a lack of technical expertise is no excuse or defence against the failure to take sufficient steps to comply with the PDPA. Even if organisations delegate work to their contractors who are their data intermediaries, organisations as data controllers must ultimately take responsibility for the personal data processed on their behalf:
3. MALICIOUS ACTIVITY
As a result of the lack of reasonable security arrangements (e.g. regular security testing and matching) to protect personal data, organisations are increasingly vulnerable to malicious actors who exploit the existing vulnerabilities.
Common examples of malicious activity include malware and phishing (where employees are tricked into revealing their login credentials or other sensitive information, or downloading attachments containing malware), as well as common brute-force attacks on the server.
We wish to highlight that being a victim of a cyberattack will not excuse the organisation from breaching any of the PDPA obligations:
A non-exhaustive list of technical security measures that can be taken to meet the Protection Obligation includes:
- Conduct regular phishing simulation exercises to train employees to be alert.
- Consider restricting Internet access especially where there is direct access from endpoints to large amounts of personal or sensitive data.
- Install endpoint security solutions as defence against malware and keep proper records of the endpoint security solutions and versions installed on all their systems and their employees’ computers.
- Ensure personal data in your organisation’s possession is automatically and regularly backed up. Backups should be stored offline and offsite for security purposes.
- Regulator patching should be carried out to protect the system against external threats. Technical measures such as firewalls should be configured carefully.
- Strong passwords should be used for administrator accounts and should be strictly enforced. Administrator accounts should also be properly managed by disabling unused or dormant accounts and deleting records. The sharing of administrator accounts should be avoided and employee access to such accounts should be monitored.
SUGGESTED WFH ARRANGEMENTS
With telecommuting expected to be the norm moving forward, some security measures that organisations can consider implementing include:
- Making sure employees are provided the proper ICT devices with appropriate security measures, and employees are held accountable for such devices. This include developing Bring Your Own Devices (BYOD) policy, implementing proper configuration and security updates, and conducting web browser hardening.
- Having an Acceptable Use Policy (AUP) that defines allowable personal uses of ICT devices and applications such as personal emails, browsing of news and articles, social media/networking sites, and video streaming sites.
- Personal data must only be made accessible on a “need-to-know” basis.
- User authentication and file security measures must be put in place. These include:
- Strong passwords to access personnel credentials and accounts.
- Set up multifactor authentication for all accounts.
- Set up policies to ensure personal data is processed in a protected and confidential manner.
- Encryption of files and attachments when transferring personal data via email.
- Retention policy for processing personal data in personal devices.
- Data Breach Management
- Employees should be aware of the organisation’s data breach policy.
- Employees must immediately notify his or her immediate supervisor in case of potential or actual breach while working from home.
- DPO should be immediately alerted of any data breach incidents.
At Infinity Legal LLC, our PDPA Practice, comprising lawyers who are Certified Personal Data Practitioners, aims to provide your organisation with a holistic, yet practical approach to complying with the PDPA. We help clients navigate through the variety of legal issues involving personal data protection.
© Infinity Legal LLC 2021
For PDF version of this article, please click here.
The content of this article is for general information purposes only, and does not constitute legal advice and should not be relied on as such. Specific advice should be sought about your specific circumstances. Infinity Legal LLC does not accept any responsibility for any loss which may arise from reliance on information or materials published in this article. Copyright in this publication is owned by Infinity Legal LLC. This publication may not be reproduced or transmitted in any form or by any means, in whole or in part, without prior written approval.
